IOT Firmware Analysis and Emulation

Requirements:
OS: AttifyOS
Tools :
firmadyne(firmware Analysis toolkit) , firmware-mod-kit(unsquashfs_all.sh, binwalk, dd )
— — — — — — — — — — — — — — — — — — — — — — — —
What is a firmware?
Firmware is a piece of code residing on a non-volatile section of a device allowing and enabling the device to perform different tasks required for the functioning of device.
It consists of various components like :
● Kernel
● Bootloader
● File system
● Additional resources
Exploiting firmware allows us to sometimes get juicy information like ssh login creds, inject backdoor for persistent access,analyse file structure of a device ,etc. So its done frequently by hackers as well as researchers. So without anymore delay lets start the fun stuff.
Following are the steps to be performed to do Firmware analysis.
1. Information gathering and reconnaissance
Acquire all relative technical and documentation details pertaining to the target device’s firmware.
IoT Auditor(app.expliot.io) is a website where we can upload our firmware image and it gives us firmware info along with analysis results.

2. Obtaining firmware
Attain firmware using one or more methods like google dorks, developer website, software dumps online, extracting from device, capturing during device update,etc.
Here is link to our testing firmware.
https://github.com/OWASP/IoTGoat/releases/download/v1.0/IoTGoat-raspberry-pi2.img
3. Analyzing firmware
Examine the target firmware’s characteristics.
We keep the copy of our firmware in firmware-mod-toolkit directory as it has various tools needed for our purpose.



4. Extracting the filesystem
Carve filesystem contents from the target firmware
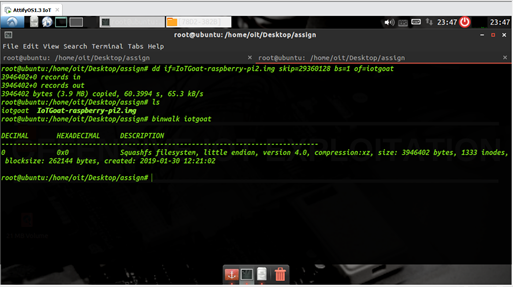

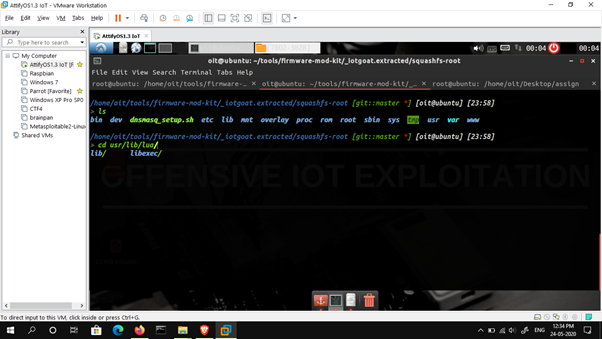
5. Analyzing filesystem contents
Statically analyze extracted filesystem configuration files and binaries for vulnerabilities.
Statically analyze filesystem contents and uncompiled code manually or leveraging automation tools such as firmwalker that parse the following:
etc/shadow and etc/passwd
list out the etc/ssl directory
search for SSL related files such as .pem, .crt, etc.
search for configuration files
look for script files
search for other .bin files
look for keywords such as admin, password, remote, AWS keys, etc.
search for common web servers used on IoT devices
search for common binaries such as ssh, tftp, dropbear, etc.
search for banned c functions
search for common command injection vulnerable functions
search for URLs, email addresses and IP addresses





6. Emulating firmware
Emulate firmware files and components
Now move the directory having your extracted firmware and firmware image to Firmadyne directory to do emulation.
We use fat tool for emulation.
(Due to some error it wasn’t loading in browser)

And now that analysis phase is complete ,we can do firmware backdooring and Dynamic/runtime analysis to get to know further about its working and potential loop holes to exploit also get root access to devices. But that’s for another time.
